The Problem
Public sector agencies face limited budgets with increasing demands, including 10%+ annual increases in service requests, straining grant management resources.
Cross-agency grant compliance workflows are fragmented, involving manual tracking from application intake through reporting and closeout, leading to errors, delays, and high administrative overhead amid complex regulatory requirements like the Single Audit Act and 2 CFR 200.
Current COTS systems are often inflexible, requiring costly customizations and lacking seamless cross-agency orchestration, resulting in insufficient audit trails and poor visibility into compliance status.
Our Approach
Key elements of this implementation
-
Workflow orchestration engine with rules-based validation for Single Audit Act (financial reporting), 2 CFR 200 (cost principles, audit thresholds), and GPRAMA (performance reporting)
-
Immutable audit trails, tamper-proof logging, and data residency controls compliant with federal standards; automated regulatory reporting dashboards
-
Native integrations with financial systems (e.g., Oracle Financials, SAP), grant platforms (e.g., Grants.gov, eCFR), and agency collaboration tools (e.g., Microsoft Teams, ServiceNow)
-
Phased rollout with 60-day pilot, human-in-the-loop reviews for high-risk approvals, executive change champions, and 4-week training to mitigate adoption risks and data quality issues
Get the Full Implementation Guide
Unlock full details including architecture and implementation
Implementation Overview
This solution delivers an end-to-end grant compliance automation platform that orchestrates workflows across agency boundaries while maintaining rigorous audit trails and regulatory adherence. The architecture centers on a rules-based workflow engine that encodes compliance requirements from the Single Audit Act, 2 CFR 200, and GPRAMA into executable validation logic, eliminating the manual tracking and offline approval processes that currently leave insufficient audit trails[3].
The platform addresses the fundamental limitation of inflexible COTS products that force agencies to spend heavily on customizations[5] by providing a configurable compliance framework that adapts to each agency's specific regulatory context while maintaining cross-agency interoperability. A federated data architecture ensures each agency retains sovereignty over its grant data while enabling coordinated compliance monitoring and consolidated reporting across jurisdictional boundaries.
Key architectural decisions prioritize auditability, cross-agency coordination, and incremental adoption. The phased rollout begins with a 60-day pilot in a single agency to establish baseline efficiency metrics before expanding to cross-agency workflows. Human-in-the-loop reviews remain mandatory for high-risk approvals throughout, with automation progressively handling routine validations as confidence in the system grows. This approach directly addresses the challenge of ensuring consistent adherence with federal, state, and local regulations[6] while managing the organizational change required for cross-agency collaboration.
UI Mockups
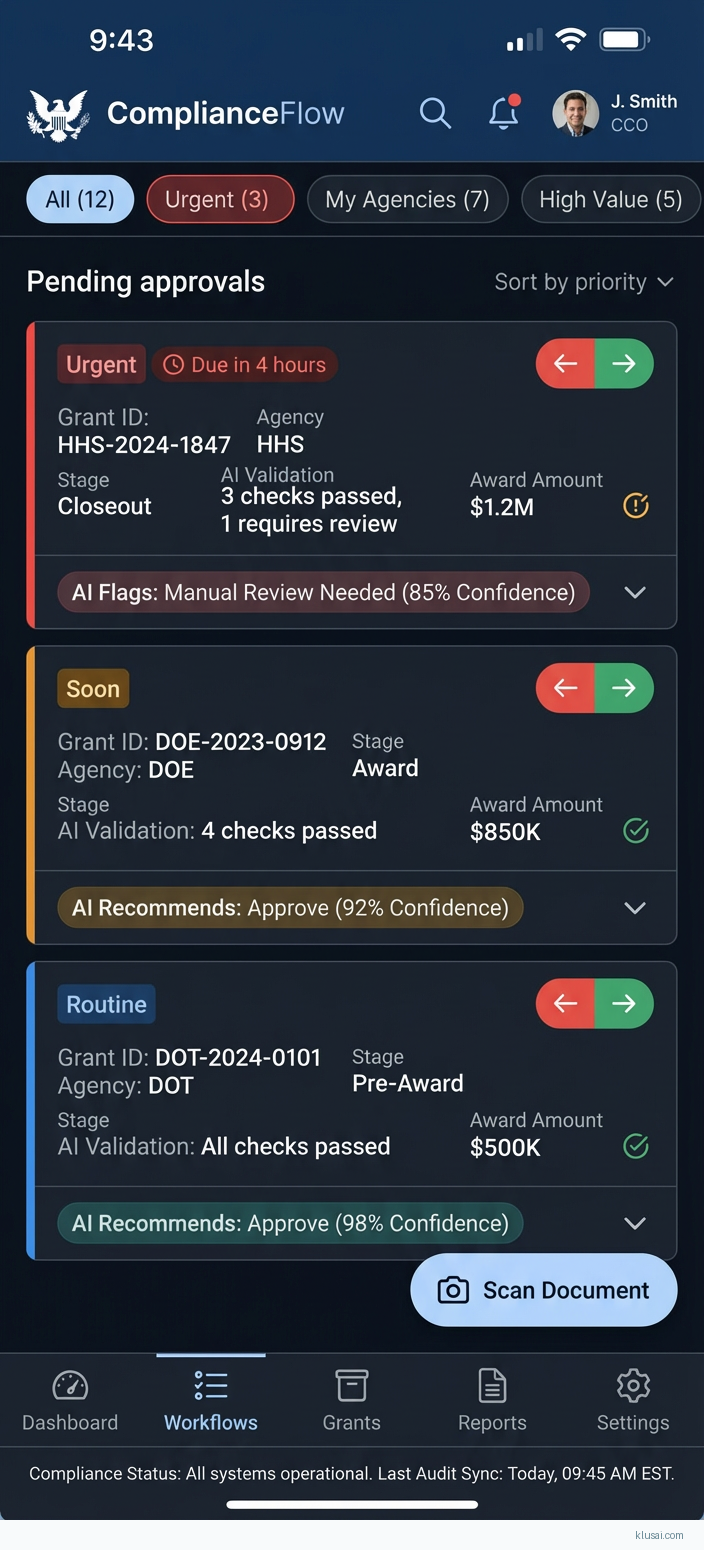
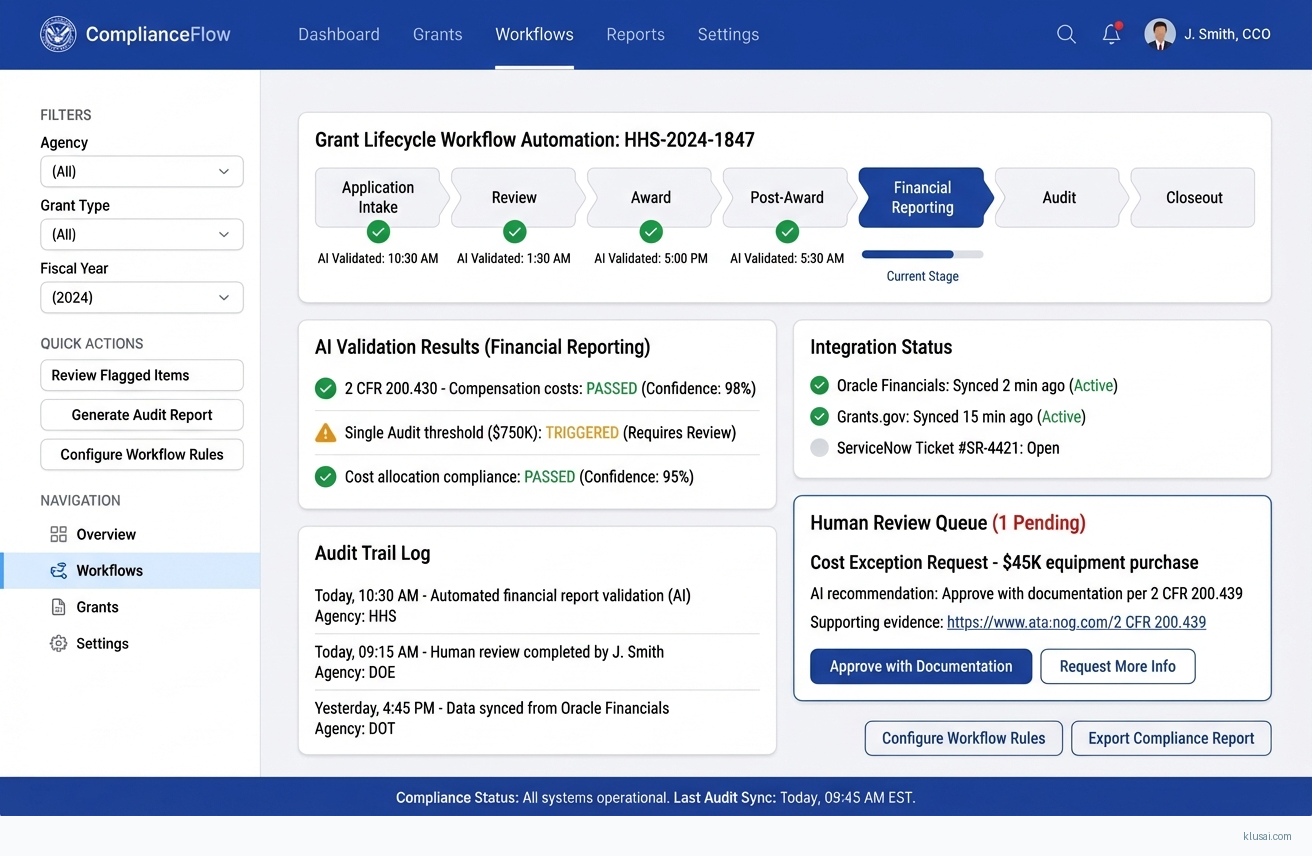
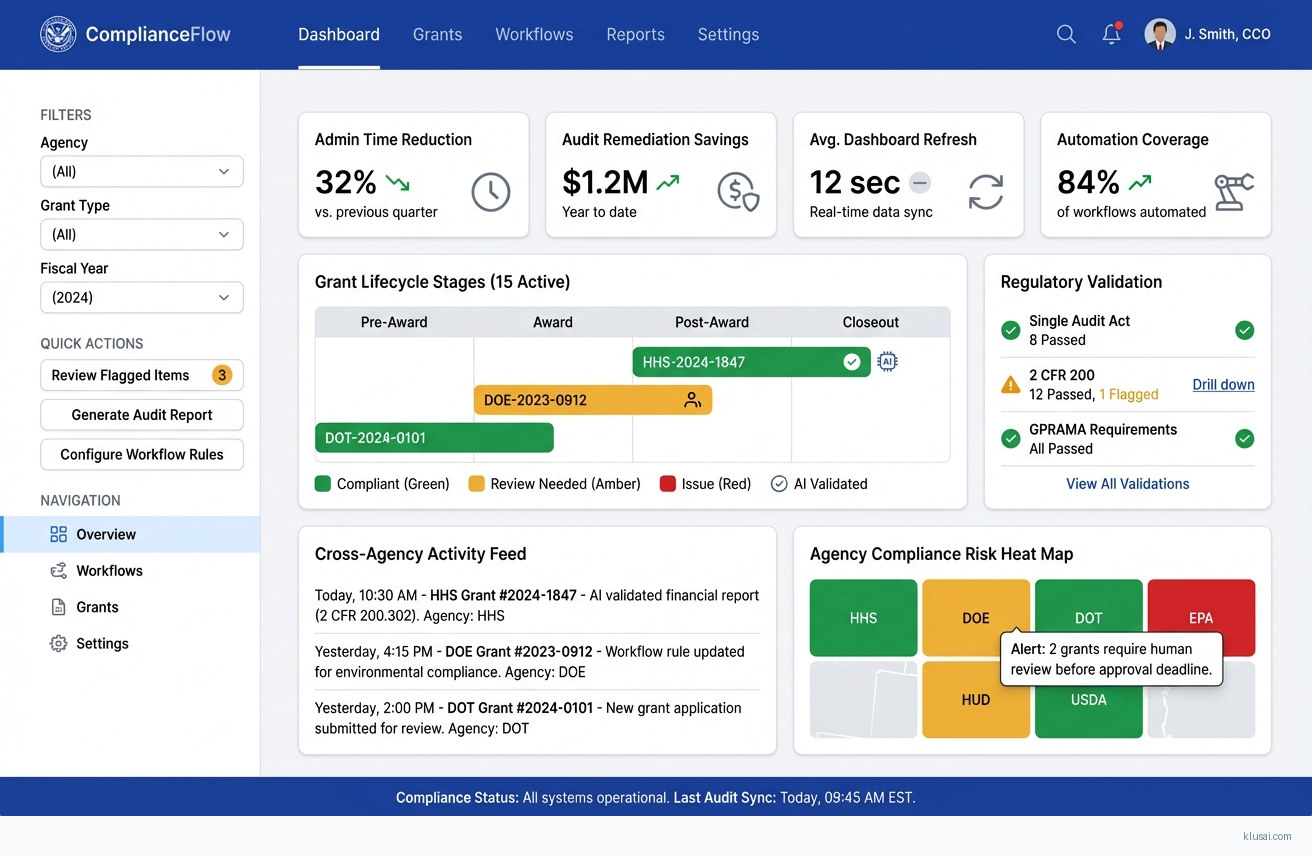
System Architecture
The architecture follows a layered approach with clear separation between workflow orchestration, compliance rules processing, data persistence, and external integrations. At the presentation layer, role-based dashboards provide grant administrators, compliance officers, and agency executives with tailored views into workflow status, compliance alerts, and cross-agency reporting.
The workflow orchestration layer implements a state machine pattern for grant lifecycle management, from application intake through closeout. Each state transition triggers compliance validation against the encoded regulatory rules, with results logged to an immutable audit store. The orchestration engine supports both synchronous validations (blocking progression until resolved) and asynchronous reviews (flagging for human attention while allowing workflow continuation for non-critical items).
The compliance rules engine maintains versioned rule sets for each regulatory framework, enabling agencies to operate under different rule versions during transition periods and supporting retrospective compliance analysis. Rules are expressed in a domain-specific language that compliance officers can review and validate without developer involvement, addressing the customization burden that plagues current COTS implementations[5].
The integration layer provides standardized connectors to financial systems, federal grant platforms, and agency collaboration tools. A message queue architecture ensures reliable delivery and enables graceful degradation when external systems are unavailable. All cross-agency data exchange occurs through a federated query model where data remains in agency-controlled storage, with only query results and aggregated metrics shared across boundaries—addressing data sovereignty concerns inherent in multi-jurisdictional deployments.
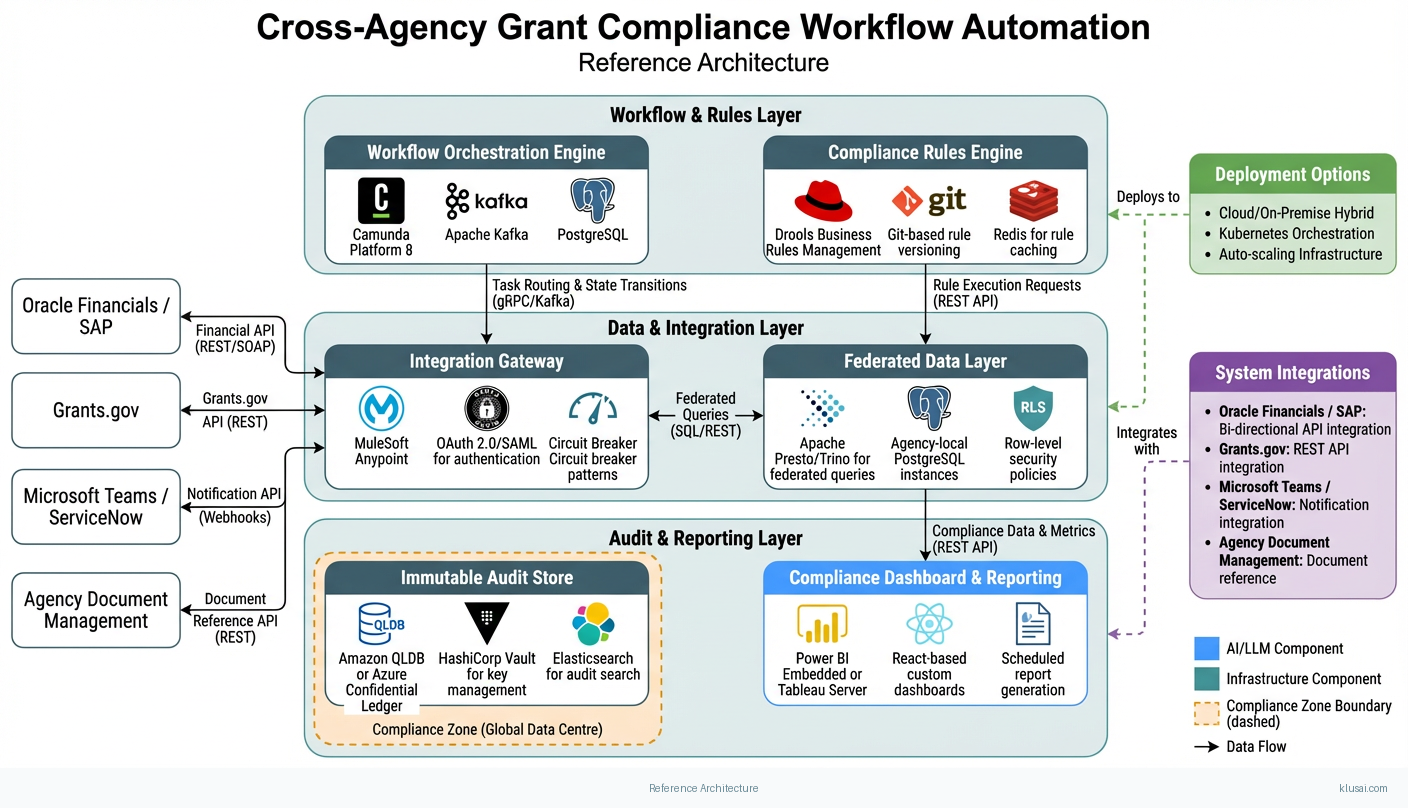
Key Components
| Component | Purpose | Technologies |
|---|---|---|
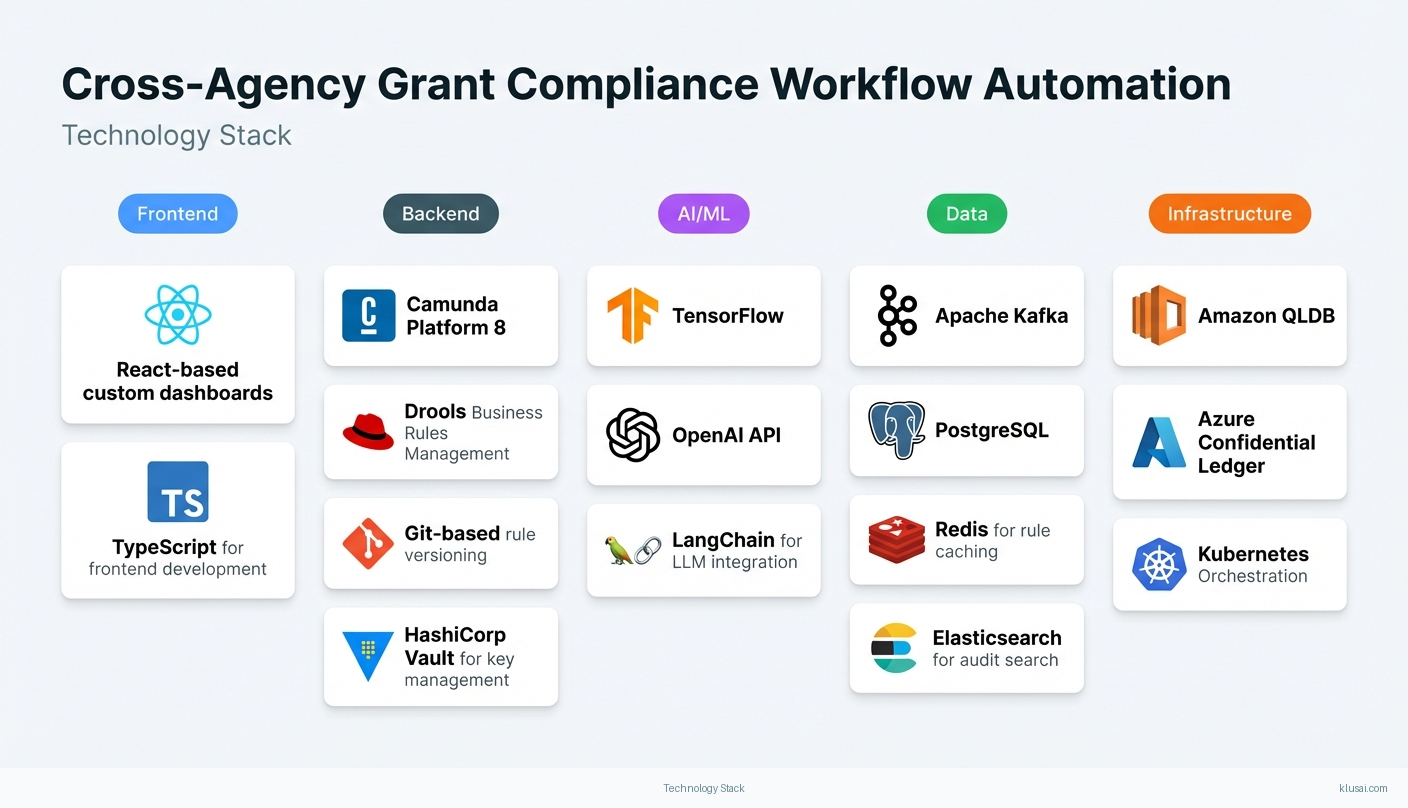
| Workflow Orchestration Engine | Manages grant lifecycle state transitions, routes tasks to appropriate reviewers, and coordinates cross-agency handoffs with configurable escalation paths | Camunda Platform 8 Apache Kafka PostgreSQL |
| Compliance Rules Engine | Encodes and executes regulatory validation logic for Single Audit Act, 2 CFR 200, and GPRAMA requirements with version control and audit logging | Drools Business Rules Management Git-based rule versioning Redis for rule caching |
| Immutable Audit Store | Provides tamper-proof logging of all compliance decisions, workflow transitions, and data access events with cryptographic verification | Amazon QLDB or Azure Confidential Ledger HashiCorp Vault for key management Elasticsearch for audit search |
| Integration Gateway | Manages connections to external systems including financial platforms, Grants.gov, and agency collaboration tools with protocol translation and retry logic | MuleSoft Anypoint or Apache Camel OAuth 2.0/SAML for authentication Circuit breaker patterns |
| Federated Data Layer | Enables cross-agency queries and reporting while maintaining data residency within each agency's controlled environment | Apache Presto/Trino for federated queries Agency-local PostgreSQL instances Row-level security policies |
| Compliance Dashboard & Reporting | Provides real-time visibility into compliance status, workflow bottlenecks, and cross-agency metrics with role-based access controls | Power BI Embedded or Tableau Server React-based custom dashboards Scheduled report generation |
Technology Stack
Implementation Phases
Foundation & Single-Agency Pilot
Deploy core workflow engine and compliance rules for pilot agency's highest-volume grant program
- • Deploy core workflow engine and compliance rules for pilot agency's highest-volume grant program
- • Establish baseline efficiency metrics through parallel operation with existing manual processes
- • Validate audit trail completeness against Single Audit Act requirements with agency compliance officers
- Production-ready workflow engine with 2 CFR 200 cost principles validation for pilot grant program
- Immutable audit store with demonstrated tamper-proof logging and 7-year retention configuration
- Baseline measurement report documenting current administrative hours per grant lifecycle stage
Integration & Workflow Expansion
Connect workflow engine to pilot agency's financial system (Oracle/SAP) and Grants.gov for application intake
- • Connect workflow engine to pilot agency's financial system (Oracle/SAP) and Grants.gov for application intake
- • Expand compliance rules to cover full 2 CFR 200 scope including audit thresholds and GPRAMA performance reporting
- • Implement human-in-the-loop review workflows for high-risk approvals with escalation paths
- Bi-directional integration with agency financial system for cost validation and drawdown tracking
- Grants.gov integration for automated application intake and status synchronization
- Complete compliance rule set covering Single Audit Act, 2 CFR 200, and GPRAMA with version control
Cross-Agency Expansion
Onboard 2-3 additional agencies with federated data architecture maintaining agency data sovereignty
- • Onboard 2-3 additional agencies with federated data architecture maintaining agency data sovereignty
- • Implement cross-agency workflow handoffs for grants involving multiple jurisdictions
- • Deploy consolidated compliance dashboards for executive visibility across participating agencies
- Federated query infrastructure enabling cross-agency reporting without data centralization
- Cross-agency workflow templates for common multi-jurisdictional grant scenarios
- Executive dashboard with real-time compliance status across all participating agencies
Optimization & Handover
Validate efficiency improvements against Phase 1 baseline with documented ROI analysis
- • Validate efficiency improvements against Phase 1 baseline with documented ROI analysis
- • Complete knowledge transfer to agency operations teams with runbook documentation
- • Establish ongoing support model and continuous improvement process
- ROI validation report comparing baseline to current state with agency-verified metrics
- Operations runbook covering monitoring, incident response, and routine maintenance
- Training completion for agency staff with certification on workflow administration
Key Technical Decisions
Should compliance rules be hardcoded in application logic or externalized in a rules engine?
Regulatory requirements change frequently (2 CFR 200 has had multiple revisions), and agencies may operate under different rule versions during transition periods. Externalizing rules enables compliance officers to review and validate rule logic without developer involvement, and supports retrospective compliance analysis against historical rule versions. This directly addresses the inflexibility of COTS products that require expensive customizations for rule changes[5].
- Compliance officers can validate rule logic in business-readable format without code review
- Supports multiple rule versions simultaneously for regulatory transitions and retrospective analysis
- Additional complexity in rule deployment pipeline and version management
- Performance overhead for rule evaluation compared to compiled application logic (mitigated by caching)
How should cross-agency data sharing be architected given data sovereignty requirements?
Public sector agencies have legitimate concerns about data sovereignty, and centralizing grant data across agencies creates both security risks and political barriers to adoption. A federated model allows each agency to maintain control over its data while enabling the cross-agency visibility needed for consolidated compliance reporting. This approach also simplifies compliance with varying data classification and retention requirements across jurisdictions.
- Each agency retains full control over its data, simplifying governance and reducing adoption barriers
- Supports varying data classification levels and retention policies across agencies
- Query performance depends on network connectivity between agencies; complex queries may be slow
- Requires each agency to maintain its own infrastructure, increasing total cost compared to centralized model
What cloud deployment model best balances security requirements with cross-agency accessibility?
Federal grant compliance requires FedRAMP authorization for cloud services handling government data. Agency-specific tenants address data sovereignty concerns while private networking (ExpressRoute/Direct Connect plus VPN mesh) enables secure cross-agency communication without public internet exposure. This model allows agencies to adopt at their own pace while maintaining interoperability.
- FedRAMP authorization satisfies federal security requirements without agency-specific ATO burden
- Agency-specific tenants provide clear security boundaries and cost allocation
- Higher infrastructure cost than shared multi-tenant model
- Cross-agency networking adds complexity and potential latency for federated queries
How should the system handle workflow continuity when external systems (Grants.gov, financial systems) are unavailable?
External system availability is outside our control, and grant workflows cannot halt entirely during outages. Circuit breakers prevent cascade failures, while queue-based integration ensures no data loss during outages. Graceful degradation allows workflows to continue with manual data entry fallbacks for unavailable integrations, with automatic reconciliation when systems recover.
- Grant workflows continue during external system outages with minimal disruption
- Automatic retry and reconciliation reduces manual intervention after outages
- Data may be temporarily out of sync during outages, requiring reconciliation logic
- Manual fallback processes must be maintained and trained even if rarely used
Integration Patterns
| System | Approach | Complexity | Timeline |
|---|---|---|---|
| Oracle Financials / SAP | Bi-directional API integration for cost validation, budget checking, and drawdown tracking. Outbound: workflow engine queries available budget and validates cost allocations against grant terms. Inbound: financial system receives approved drawdown requests and returns transaction confirmations. Real-time for budget checks, batch for reconciliation. | high | 6-8 weeks |
| Grants.gov | REST API integration for application intake and status synchronization. Poll for new applications and status changes on configurable schedule (typically hourly). Transform Grants.gov XML schemas to internal data model. Handle rate limits with exponential backoff. | medium | 3-4 weeks |
| Microsoft Teams / ServiceNow | Notification and task integration for human-in-the-loop workflows. Teams: adaptive cards for approval requests with inline action buttons. ServiceNow: create incidents for compliance exceptions, update workflow status from ServiceNow ticket resolution. Webhook-based for real-time notifications. | low | 2-3 weeks |
| Agency Document Management (SharePoint, FileNet) | Document reference integration—store document metadata and links in workflow system, documents remain in agency DMS. Retrieve documents on-demand for compliance review. Support check-out/check-in for document updates during workflow. | medium | 3-4 weeks |
ROI Framework
ROI is driven by administrative time savings from automated compliance validation and workflow routing, reduced audit remediation costs from improved documentation and proactive compliance monitoring, and capacity release enabling agencies to handle increasing service volumes without proportional staff increases[1][2]. Efficiency improvement estimates should be validated during the 60-day pilot phase with agency-specific baseline measurements.
Key Variables
Example Calculation
Build vs. Buy Analysis
Internal Build Effort
Internal build would require 18-24 months with a team of 8-12 FTEs including workflow developers, integration specialists, compliance analysts, and DevOps engineers. Key challenges include: (1) maintaining compliance rule currency as regulations change—2 CFR 200 alone has had multiple revisions requiring rule updates; (2) building cross-agency orchestration capabilities with appropriate security and governance; (3) achieving the audit trail rigor required for federal compliance, which current offline processes fail to provide[3]. Estimated internal build cost: $2-3M over 24 months, plus ongoing maintenance of $400-600K annually for a team to maintain integrations and update compliance rules.
Market Alternatives
Salesforce Public Sector Solutions
$150-300K annually depending on user count and modules; implementation $200-400KEnterprise platform with strong CRM foundation and FedRAMP authorization. Best suited for agencies already invested in Salesforce ecosystem seeking unified constituent and grant management on a single platform.
- • FedRAMP authorized with established government customer base
- • Strong ecosystem of implementation partners and pre-built government components
- • Grant management is add-on to CRM core; compliance workflow automation requires significant customization
- • Cross-agency orchestration requires additional integration work beyond standard platform
ServiceNow Public Sector Digital Services
$200-400K annually for public sector modules; implementation $250-500KIT service management platform extended to government workflows. Strong choice for agencies with existing ServiceNow investment seeking to consolidate workflow automation on single platform.
- • Robust workflow engine with visual designer and strong audit capabilities
- • Existing government deployments with established security posture
- • Grant-specific compliance rules (2 CFR 200, Single Audit Act) require custom development
- • Licensing model can become expensive as user count and workflow complexity grow
Grants.gov Workspace + Agency Custom Development
No licensing for Grants.gov; custom development $500K-1.5M depending on scopeFederal standard for grant application management with agency-specific backend systems. Suitable for agencies prioritizing federal system alignment and willing to invest in custom compliance automation.
- • No licensing fees for federal platform; standard interface for federal grant programs
- • Direct integration with federal grant ecosystem
- • Limited workflow automation capabilities; primarily application intake focused
- • Requires significant custom development for compliance monitoring and cross-agency coordination
Our Positioning
KlusAI's approach is ideal for agencies requiring deep customization of compliance rules, cross-agency orchestration capabilities, or integration with diverse legacy systems where COTS products would require extensive—and expensive—customization[5]. We assemble teams with specific expertise in federal grant compliance, workflow automation, and government system integration, providing the flexibility to adapt the solution to each agency's unique regulatory and operational context. This is particularly valuable when agencies need to move faster than typical government procurement cycles allow, or when cross-agency governance complexity makes standard products insufficient.
Team Composition
KlusAI assembles specialized teams tailored to each engagement, drawing from our network of professionals with public sector, compliance, and enterprise integration experience. The team composition below represents a typical engagement structure, adjusted based on agency size, number of participating agencies, and integration complexity.
| Role | FTE | Focus |
|---|---|---|
| Engagement Lead / Solutions Architect | 1.0 | Overall solution architecture, stakeholder management across agencies, and delivery oversight |
| Compliance Rules Analyst | 0.75 | Translating regulatory requirements (2 CFR 200, Single Audit Act, GPRAMA) into executable rule definitions |
| Workflow Developer | 1.5 | Implementing workflow orchestration, state management, and cross-agency handoff logic |
| Integration Engineer | 1.0 | Building and maintaining connections to financial systems, Grants.gov, and agency collaboration tools |
| DevOps / Platform Engineer | 0.75 | Infrastructure automation, CI/CD pipelines, monitoring, and security configuration |
Supporting Evidence
Performance Targets
25-35% reduction from baseline
50% reduction in first full audit cycle post-implementation
Real-time dashboard availability for all participating agencies within 30 seconds of status change
>80% of routine compliance validations automated by end of Phase 3
Team Qualifications
- KlusAI's network includes professionals with federal grant management and compliance experience across civilian and defense agencies
- Our teams are assembled with specific expertise in workflow automation platforms (Camunda, ServiceNow) and government system integration
- We bring together technical architects and domain specialists with experience navigating cross-agency governance and data sharing agreements
Source Citations
10%+ annual increase in service requests
directionalincreasing demands on grant management
directionaloffline approval processes... do not leave a sufficient audit trail
"offline approval processes do not leave a sufficient audit trail if questions arise"directional
COTS products for Grants management that can be inflexible, forcing... customisations
"Commercial, off-the-shelf (COTS) products for Grants management that can be inflexible, forcing government organisations to spend more on customisations"exact
strong grant management... ensure consistent adherence with federal, state and local regulations
directionalReady to discuss?
Let's talk about how this could work for your organization.
Schedule a Consultation
Pick a date that works for you
Times shown in your local timezone ()
Prefer email? Contact us directly
Almost there!
at
Your details
at
You're all set!
Check your email for confirmation and calendar invite.
Your booking is confirmed! Our team will reach out to confirm the details.
Your consultation
· min
( team time)
Quick Overview
- Technology
- Process Automation
- Complexity
- high
- Timeline
- 5-7 months
- Industry
- Public Sector